Ever really feel like each MDR supplier is promising “round the clock safety” however nobody tells you what that truly seems to be like at 2 a.m. throughout a stay ransomware incident?
Similar. I’ve spent the final two years researching and writing about cybersecurity, overlaying all the things from zero belief to risk intelligence, and I’ve had numerous conversations with safety leads, analysts, and IT groups caught in alert fatigue.
One factor all of them need? A companion, not only a product. So I made a decision to chop by the buzzwords and consider 15+ distributors to determine the high MDR suppliers who really ship when it issues most. Not simply quick SLAs and glossy dashboards, however hands-on assist once you’re short-staffed, and proactive risk searching when your in-house group’s swamped.
When you’re out there for MDR, chances are high you already know the stakes. Whether or not you are battling useful resource constraints, coping with government strain to show ROI, or simply attempting to keep away from changing into the subsequent breach headline, this information is for you.
I’ve damaged down what actually units the perfect MDR companies aside, from service high quality and analyst entry to how they deal with escalation, onboarding, and integration together with your present stack.
Let’s get into the highest MDR suppliers that earned my confidence, impressed many G2 customers, and may simply win your group’s belief too.
6 high MDR suppliers for 2025: My high picks
| MDR service supplier | Greatest for | Standout characteristic | Pricing |
| Huntress Managed EDR | Small companies with restricted IT employees | 24/7 SOC with quick detection, guided remediation | Customized pricing |
| Sophos MDR | Mid-market and enterprise in search of layered safety | 24/7 SOC with quick detection, guided remediation, | Customized pricing |
| Arctic Wolf | Organizations needing concierge-style help | Named concierge safety group (CST) with proactive steering | MDR Fundamental Monitor (as much as 100 customers with MDR) prices $44,000 per yr, in response to AWS Market information |
| ThreatDown | SMBs and MSPs in search of automation + SOC | Clear pricing bundles and ransomware rollback constructed into core plans | Begins at $ 345 per yr for five units |
| Blackpoint Cyber | MSPs and SMBs needing fast, aggressive response | Direct call-in help and stay containment actions with out further approval steps | Customized pricing |
| Purple Canary | Safety-mature groups that need deep visibility | Versatile telemetry assortment from present EDR instruments plus clear analyst context on each alert | Begins at $120 per endpoint/yr (Consumer accounts $100/yr, cloud sources $250/yr, community $20/yr), in response to AWS market information. |
*These MDR suppliers are top-rated of their class, in response to G2 Grid Stories.
6 high MDR suppliers I recommend after evaluating 15+ instruments
Outsourcing safety isn’t new. I’ve seen corporations depend on managed safety service suppliers (MSSPs) for the reason that late ’90s. However MDR is a distinct breed. In contrast to conventional MSSPs that largely ahead logs and alerts, MDR really helps you determine what’s occurring and what to do subsequent. It combines know-how with actual human analysts who detect, examine, and reply to threats in actual time.
For lean, overworked safety groups, that shift from passive monitoring to hands-on response is defining, and I’ve come to actually recognize it extra given the character of safety incidents today. 88% of ransomware assaults happen exterior regular enterprise hours, and practically 4.75 million cybersecurity employees are wanted to fill the workforce hole at this time.
What shocked me most as I in contrast MDR suppliers is how related they sound, till you look nearer. “24/7 SOC,” “risk searching,” “real-time response” — it’s all on the web site. However what really separates the good from the nice is the expertise: how briskly they act, how nicely they perceive your setting, and the way usually you’re left guessing.
The perfect managed detection and response software program don’t simply combine together with your stack. They combine together with your group. And that makes all of the distinction.
How did I discover and consider the highest MDR suppliers?
I began with G2’s Grid Stories, my go-to supply for actual, unbiased consumer suggestions, to construct a shortlist of greatest MDR companies. I checked out a mixture of well-established leaders and rising gamers with robust rankings.
Since MDR is a high-touch, always-on service, most suppliers supply demos however not free trials. So I centered on researching every product’s technical capabilities, from supported integrations to response playbooks, and dug deep into consumer evaluations to know what actual customers say about their on a regular basis expertise and outcomes.
After I couldn’t strive or demo a platform firsthand, I consulted cybersecurity professionals with direct expertise and cross-referenced their insights with G2 suggestions.
So as to add context, I used AI instruments to research tons of of G2 evaluations. It helped me spot constant strengths like quick response and analyst help, and crimson flags like alert fatigue or poor integrations.
The screenshots featured on this article are a mixture of visuals taken from G2 vendor pages and publicly accessible product supplies.
What makes the highest MDR suppliers: My standards
As soon as I narrowed down the highest MDR distributors, I centered on the technical capabilities, operational strengths, and hands-on worth that make a supplier stand out. Listed here are the important thing standards I used to judge them:
- Actual-time risk detection and speedy response: Pace is all the things in fashionable risk protection. I appeared for suppliers providing true 24/7 monitoring with the flexibility to detect, triage, and reply to threats in close to real-time. This contains endpoint isolation, account lockout, or containment on the community stage, ideally inside minutes of detection.
- Direct entry to skilled safety analysts: Automated alerts solely go to date. I wished to know if there have been human analysts behind the scenes. The highest suppliers provided entry to their SOC (safety operations middle) across the clock, with devoted analysts who not solely validate threats but additionally present tailor-made remediation steering by post-incident evaluation when wanted.
- Integration with the prevailing safety stack: My precedence was to keep away from groups beginning from scratch. The perfect MDRs help seamless integration with instruments already in use, whether or not that’s Microsoft Defender, SentinelOne, CrowdStrike, Okta, or AWS. I additionally appeared for pre-built integrations with SIEMs, ticketing programs, and cloud-native platforms to attenuate friction and maximize visibility.
- Excessive signal-to-noise ratio: It’s straightforward for an MDR to floor each suspicious occasion. What’s arduous and priceless is filtering out the noise. I evaluated how nicely every supplier enriches alerts with context (like consumer conduct or asset sensitivity), minimizes false positives, and gives actionable intelligence that safety groups can belief and act on shortly.
- Customizable response playbooks and escalation paths: Incident response isn’t one-size-fits-all. I prioritized distributors that allow the groups outline response thresholds and customise escalation workflows. That meant configuring when they need to isolate a tool, notify particular contacts, and defer to inner coverage, giving me management whereas nonetheless offloading the grunt work.
- Time to deploy and onboarding high quality: MDR options don’t ship worth on day one; their deployment and tuning matter. I assessed how lengthy it usually takes to rise up and working, what sort of onboarding help is supplied, and whether or not they assist with tuning detection guidelines, integrating throughout the setting, and educating inner groups on what to anticipate.
- Visibility, transparency, and reporting: I didn’t need a black field. I wished a partnership. Which means full visibility into energetic threats, response actions, and incident timelines by a stay portal or common stories. Some suppliers supply analyst notes, root trigger breakdowns, and MITRE ATT&CK mapping so as to add deeper context. These have been large pluses.
- Compliance and audit readiness: For any group topic to HIPAA, PCI-DSS, NIST, or SOC 2, MDR suppliers must help compliance efforts, not hinder them. I appeared for options like detailed incident logs, report exports, information retention insurance policies, and alignment with compliance frameworks to make sure audit readiness.
The listing beneath comprises real consumer evaluations from the platform software program class. To be included on this class, an answer should:
- Monitor shopper networks and endpoints for safety incidents
- Resolve threats on the shopper’s behalf
- Present these managed companies with out the necessity for shopper help
*This information was pulled from G2 in 2025. Some evaluations could have been edited for readability.
1. Huntress Managed EDR: Greatest for speedy response and analyst help
Huntress Supervisor EDR shortly made its technique to the highest of my listing of MDR service suppliers, and it wasn’t arduous to see why. From the second I checked out it, it was clear this wasn’t simply one other EDR software with MDR slapped on.
One of many first issues I observed? Deploying Huntress is refreshingly easy. Whether or not you’re putting in it through a script or utilizing your RMM, it’s fast, environment friendly, and doesn’t depart you guessing. No bloated onboarding course of. Only a light-weight agent that will get to work nearly instantly with out hogging system sources. Actually, Huntress EDR is commonly thought to be a number of the greatest MDR software program for small enterprise safety.
G2 Information additionally says the identical factor. The platform persistently scores nicely above common for ease of use (96%) and ease of setup (97%), making it probably the most user-friendly MDR software program choices on the market, particularly for small or mid-sized companies. And for safety groups which might be lean or stretched skinny, that simplicity means a quicker path to safety.
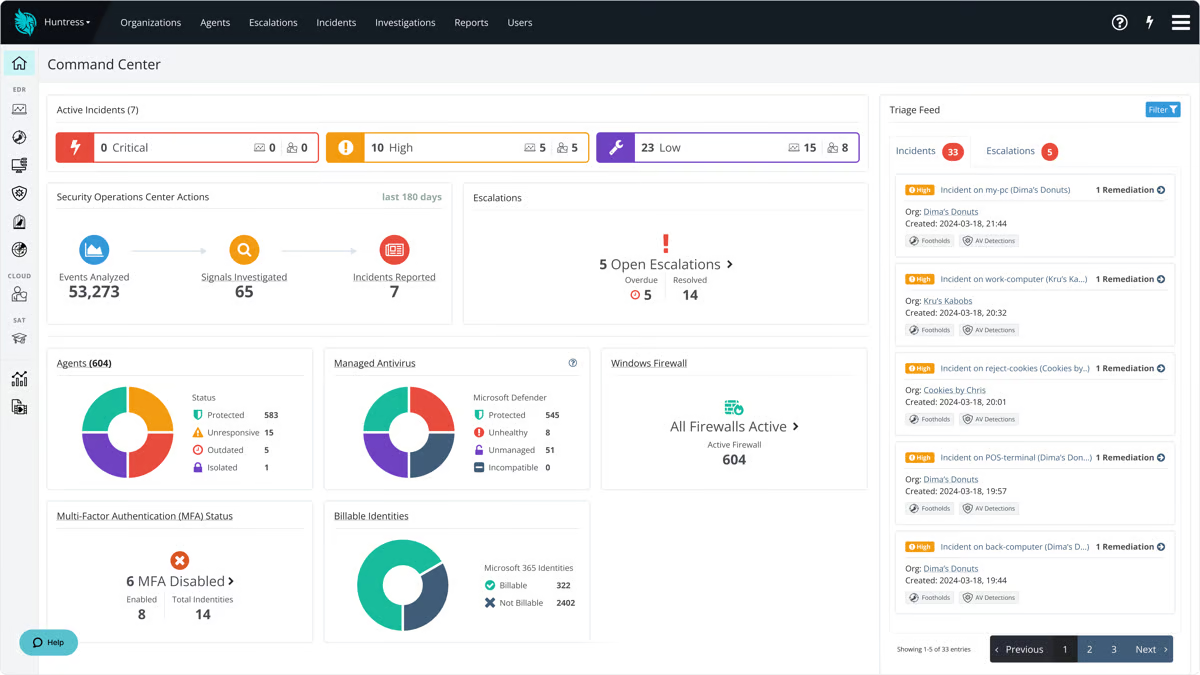
The place Huntress shines for me is the totally staffed 24/7 Safety Operations Middle (SOC) that truly watches your again. This isn’t some “set it and neglect it” software program. If one thing’s off, actual analysts evaluate it, examine it, and ship actionable stories.
The reward from customers can also be loud and constant: practically each evaluate talked about how responsive the group is and the way efficient the platform is at real-time risk detection. Actually, customers rated its 24/7 help, proactive risk searching, and speedy response time at 96% and above, which isn’t simply spectacular; it’s one of many category-leading scores.
One other standout I noticed? Ransomware canaries. That is most likely one in every of my favourite options. Mainly, Huntress crops decoy information throughout your setting. If ransomware begins encrypting them, it triggers an on the spot alert. No extra ready till half your community is locked down. It is intelligent and easy, and it really works.
That mentioned, a few issues stood out in consumer suggestions. First, in case your group is heavy on Macs, you’ll wish to plan forward. MacOS deployment with Huntress tends to be extra hands-on than Home windows, particularly in the case of permissions and configuration. Nonetheless, I preferred that Huntress is upfront about this and gives clear documentation to information groups by the method, one thing customers persistently known as out in a constructive gentle.
There have been additionally a couple of lighter mentions throughout G2 evaluations, corresponding to occasional noisy alerts throughout busy durations or a need for extra customization in reporting. Typically, these didn’t come up usually and have been famous as minor enhancements that have been wanted.
Would I like to recommend it? Completely. When you’re an IT lead at a small enterprise, an MSP juggling a number of shoppers, or perhaps a startup with restricted inner safety sources, Huntress delivers.
What I like about Huntress Managed EDR:
- From all the things I gathered, ease of setup and use is a transparent win — customers persistently mentioned they have been up and working quick, and that the interface felt intuitive even for smaller groups.
- One factor I stored seeing in evaluations was how robust and responsive the analyst help is. When customers bumped into points, they didn’t simply get alerts. They received actual assist from people who know what they’re doing.
What G2 customers like about Huntress Managed EDR:
“As a small MSP, it’s comforting realizing that I’ve Huntress Labs Managed MDR put in and defending my shoppers’ computer systems. Their help is nearly as good as any I’ve seen. Most significantly, realizing if one thing ought to occur, I’ve their extremely skilled SOC on the prepared to help in remediating the difficulty.
In contrast to another merchandise I examined, Huntress is great about retaining a low profile and controlling the quantity of noise. It was surprisingly straightforward to implement. I additionally very very like their dashboard, which makes it straightforward to watch the safety well being of my shoppers’ computer systems. I am proud of my resolution to go along with Huntress MDR and have just lately begun rolling out their ITDR module to my clients.”
– Huntress Managed EDR Evaluation, Richard G.
What I dislike about Huntress Managed EDR:
- A number of customers identified that macOS deployment takes extra effort than Home windows, particularly in the case of permissions and preliminary setup.
- There have been additionally a couple of mentions of alert noise and restricted reporting customization. Whereas not main complaints, they could be price noting for groups with complicated wants.
What G2 customers dislike about Huntress Managed EDR:
“Huntress was a little bit sluggish on getting MAC compatibility working, they have been upfront about it and had a practical timetable, nevertheless it nonetheless took a bit.”
– Huntress Managed EDR Evaluation, Jacob S.
MDR instruments usually work greatest when paired with a robust endpoint detection and response (EDR) basis. Discover our in-depth information to the greatest EDR software program to match distributors, see evaluations, and perceive how EDR matches right into a layered safety technique.
2. Sophos MDR: Greatest for midsize and enterprise groups needing unified safety
Sophos MDR is a type of names you hear time and again, whether or not you’re speaking to a lean IT group at a midsize enterprise or a safety advisor cleansing up after an incident. So I wished to see for myself whether or not the popularity matched the truth.
What stood out to me fairly shortly was how Sophos approaches managed detection and response much less like a bolt-on service and extra like an evolution of their whole platform.
When you’re already utilizing Intercept X, Sophos Firewall, or their cloud safety instruments, Sophos MDR integrates nearly seamlessly. You get a single, unified view in Sophos Central as an alternative of juggling a number of consoles or fragmented alerts.

Even in the event you depend on third-party information sources like Microsoft 365 or AWS, the MDR group can nonetheless monitor and reply successfully; it simply takes a bit extra setup to attach all the things. Both method, the expertise is designed to really feel cohesive, not like an add-on pasted over your setting.
That tracks with what customers say. The satisfaction ranking of Sophos MDR stands at 94–95% for ease of setup, ease of use, and ease of admin.
Sophos provides you a transparent alternative in how incidents are dealt with by its MDR Ops group, which I believe is one in every of its strengths. You may choose Collaborate mode, the place the MDR group investigates threats and retains you accountable for any containment actions, or Authorize mode, the place they proactively neutralize threats and loop you in afterward. It’s a sensible mannequin that feels extra versatile than what you get with many MDR suppliers, the place you both must do all the things your self or hand over full management by default.
I additionally observed Sophos persistently will get robust marks for 24/7 help, proactive risk searching, and speedy response time, with satisfaction rankings above 95%.
I discovered the weekly and month-to-month stories priceless. They provide you a transparent snapshot of risk exercise, response actions, and general well being throughout your setting, so that you’re not left questioning what’s occurring behind the scenes.
Nonetheless, fairly a couple of G2 reviewers talked about that report customization feels a little bit restricted, especially in the event you want granular or compliance-specific particulars past the defaults.
Additionally, I did see a couple of feedback about alert tuning and false positives. To fight this subject, some groups talked about spending further time reviewing detections to make sure they have been actionable. To be truthful, false positives are fairly widespread throughout most MDR options, so I wouldn’t take into account them distinctive to Sophos.
General, in the event you’re trying to find an MDR service supplier that balances sturdy protection with choices to remain hands-on (or allow them to take over when wanted), Sophos MDR makes a robust case. I’d suggest it to midsize and enterprise safety groups, particularly in industries the place compliance and quick escalation matter.
What I like about Sophos MDR:
- From what I’ve learn, integration is an enormous energy. Many reviewers mentioned they have been capable of get Sophos MDR working shortly, particularly in the event that they have been already utilizing different Sophos instruments like Intercept X.
- I observed a number of constructive suggestions about 24/7 analyst help and proactive risk searching, which persistently scored above 95% satisfaction.
What G2 customers like about Sophos MDR:
“Since implementing Sophos MDR, we have now skilled a major enchancment in our safety posture. Sophos MDR actively displays our community and login exercise, and so they have alerted us to suspicious conduct on our Entra account inside only one to 2 hours of compromise. Furthermore, they supply clear, step-by-step remediation steering, which has been invaluable. For our on-premises infrastructure, we’ve configured the system to permit Sophos to autonomously tackle any points they detect.”
– Sophos MDR Evaluation, Stephen S.
What I dislike about Sophos MDR:
- Few G2 reviewers talked about that report customization feels restricted, particularly in the event you want extra granular or compliance-focused particulars past the default dashboards.
- I additionally got here throughout feedback about occasional false positives or needing further alert tuning, which might take further time to kind by and prioritize.
What G2 customers dislike about Sophos MDR:
“Whereas Sophos MDR is general a robust answer, there are a couple of areas for enchancment. Generally the alerts is usually a bit too frequent or not totally prioritized, which might result in alert fatigue. Moreover, the response time from the MDR group, whereas normally quick, can often be slower throughout non-critical points. Pricing may also be a priority for smaller organizations, because the service can change into pricey relying on the variety of units or endpoints.”
– Sophos MDR Evaluation, Alan L
3. Arctic Wolf: Greatest MDR for visibility throughout your safety setting
When you’re exploring methods to strengthen your safety with out constructing a whole SOC from scratch, Arctic Wolf’s Managed Detection and Response (MDR) is price a glance. I’ve spent a while digging into how the MDR service supplier works, and right here’s what stood out to me.
Once you join, you’re paired with what they name a concierge safety group (CST), principally, a bunch of safety professionals who change into an extension of your IT employees, just like what Huntress and Sophos MDR present. They assist you to set up their sensors, brokers, and cloud connectors to watch your cloud setting.
From what I’ve learn, that concierge method isn’t only a advertising time period. In G2 evaluations, customers persistently rated Arctic Wolf extremely for twenty-four/7 help, proactive report alerts, and speedy response time, with satisfaction scores within the 95–98% vary.

A number of groups talked about that having a predictable level of contact made it a lot simpler to remain forward of points, particularly in industries like healthcare, finance, and manufacturing, the place compliance necessities and incident timelines can get difficult shortly.
The convenience of setup and ease of administration have been additionally a shiny spot, with rankings that hovered round 92%, which is spectacular provided that MDR deployments normally include loads of transferring elements. Many G2 customers described the onboarding course of as structured and thorough, and mentioned the day-to-day expertise didn’t require fixed oversight as soon as all the things was in place.
One of many different issues I stored coming throughout in evaluations was how robust the visibility is throughout your setting as soon as Arctic Wolf is totally arrange. From all the things I’ve learn, the platform appears to offer groups a stage of readability they didn’t have earlier than.
Whether or not it’s recognizing developments in endpoint conduct, correlating logs from totally different instruments, or simply realizing the place to focus first when one thing seems to be off, a number of customers mentioned it made them really feel extra assured about what was occurring throughout their community. For smaller groups that wish to know precisely the place they stand by way of safety, that sort of visibility is usually a big benefit.
In fact, there are a couple of trade-offs to concentrate on. One theme I observed in evaluations is that Arctic Wolf isn’t low cost, particularly for smaller organizations or public sector groups watching their budgets carefully. Many customers mentioned the worth was price it, however the worth is usually a hurdle.
One other factor that got here up was the portal and dashboards, which some groups felt could possibly be extra user-friendly or versatile. A number of reviewers talked about that navigating all the info takes some getting used to and that they’d like extra customization choices to kind and prioritize what issues most.
That mentioned, in case you are searching for an MDR answer that delivers robust help and a high-touch expertise, Arctic Wolf is simple to suggest. It is persistently acknowledged among the many main MDR companies for monetary companies companies, healthcare, and different regulated industries that want predictable help and powerful visibility.
What I like about Arctic Wolf:
- I recognize how hands-on the concierge safety group is. A number of customers mentioned having named contacts and constant steering made them really feel like they’d a real companion, not simply one other vendor.
- I discover it priceless that the platform gives robust visibility throughout the setting, serving to groups see patterns, correlate logs, and keep forward of points with out feeling at nighttime.
What G2 customers like about Arctic Wolf:
“Arctic Wolf’s capability to realize broad visibility in my setting helps me with the notice that I could not have had in any other case. Additionally, I really like the Concierge Safety Crew working with me, reviewing my setting to assist discover and shut gaps.”
– Arctic Wolf Evaluation, Joe M.
What I dislike about Arctic Wolf:
- Price is usually a barrier, in response to G2 reviewers, particularly for smaller organizations or these with tight budgets.
- I additionally noticed suggestions in regards to the portal and dashboards typically being difficult to navigate, with a studying curve to get all the things tuned the way in which you need.
What G2 customers dislike about Arctic Wolf:
“The one actual draw back is price. Nonetheless, they aren’t far off from different distributors on this space.”
– Arctic Wolf Evaluation, Matthew Ok.
4. Threatdown: Greatest for reasonably priced MDR
I’ve recognized Malwarebytes for fairly a while, however I wished to see how ThreatDown, provided by the corporate, holds up once you look previous the model identify and give attention to what customers really expertise daily.
The factor I recognize is how upfront ThreatDown is about pricing. Actually, the pricing half alone is a large plus for me. So many MDR distributors make you leap by hoops simply to determine what you’ll pay, however ThreatDown lays all of it out clearly. For groups that don’t have time to barter forwards and backwards, that stage of transparency round packages is refreshing.
I spent a while wanting into what you really get in every plan. Even the Superior bundle contains some strong capabilities like ransomware rollback, EDR, patch administration, firewall administration, and managed risk searching, which is much more than fundamental antivirus. When you step as much as the Elite plan, you get 24/7 managed risk detection, searching, investigation, and remediation, which feels nearer to a real around-the-clock SOC expertise.
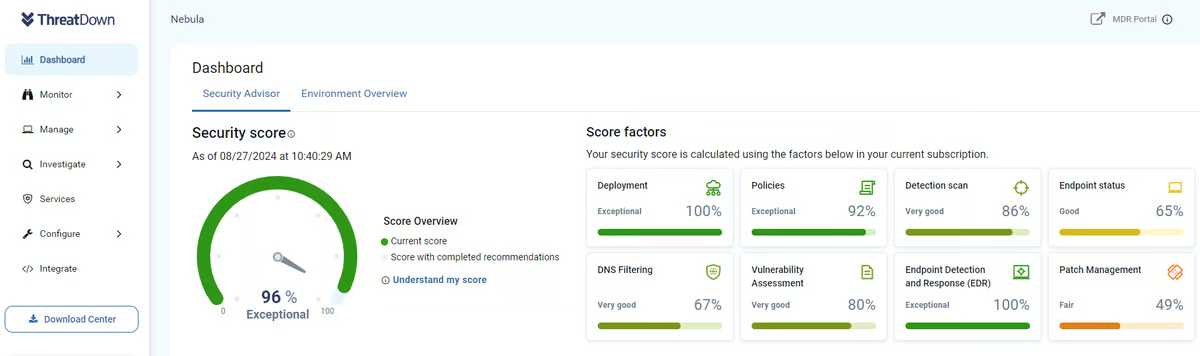
ThreatDown delivers the core capabilities you’d anticipate from the MDR: steady monitoring, proactive risk searching, and incident response help. However what appears to resonate most with clients and truthfully stood out to me as I learn by evaluations is how the service makes the superior risk detection approachable.
As an alternative of forcing your group to change into specialists in managing detection guidelines or correlating logs, ThreatDown’s analysts do the heavy lifting behind the scenes. They gather and analyze telemetry throughout your setting, determine suspicious behaviors, and escalate confirmed threats with clear, actionable steering. I got here throughout a number of examples the place customers mentioned this method reduce down on alert fatigue and helped them give attention to actual points as an alternative of spending hours sorting by noise.
Options like speedy response time (93% satisfaction), proactive report alerts (91%), and automatic investigation (91%) have been all among the many highest-rated areas on G2. Even its automated remediation capabilities are rated 90%, exhibiting that clients persistently discover worth in ThreatDown’s capability to shortly neutralize threats with out fixed handbook intervention.
And if you should tailor your reporting, 86% of customers reported being glad with the platform’s customizable stories, in response to G2 Information.
That mentioned, there have been a few drawbacks price noting. Some customers described inconsistent buyer help, saying their expertise depended rather a lot on which engineer dealt with their case, which could possibly be difficult throughout time-sensitive incidents. I additionally noticed suggestions about communication gaps, like not at all times getting clear updates when new options have been launched or when the rebrand occurred.
On the entire, although, most groups nonetheless rated ThreatDown extremely for day-to-day reliability and felt it delivered robust safety with out overwhelming complexity.
When you’re searching for an MDR answer that prioritizes pace, simplicity, and a transparent path to operational safety, ThreatDown is price contemplating.
I’d particularly suggest it for IT groups in mid-sized organizations, manufacturing, authorities, or training, the place you want robust protection with out a steep studying curve. For a lot of groups, it’s a user-friendly and adaptable MDR software for companies that need robust safety with out the complexity of enterprise platforms.
What I like about ThreatDown:
- I discover it priceless that ThreatDown is clear about pricing and bundles, which makes planning and budgeting rather a lot easier in comparison with different MDR choices.
- I actually like that even within the extra reasonably priced plans, clients get ransomware rollback, patch administration, and managed risk searching, options not at all times included in entry-level MDR instruments.
What G2 customers like about ThreatDown:
“ThreatDown may be very user-friendly with an intuitive interface that makes risk detection and response easy. The software gives fast insights into safety threats, simplifying my workflow considerably. Your paying for a top quality product.”
– ThreatDown Evaluation, Carlos P.
What I dislike about ThreatDown:
- Some reviewers talked about inconsistent buyer help, the place the extent of assist relied on which engineer you labored with.
- I got here throughout suggestions about communication gaps, like not at all times getting well timed updates when options change or when new capabilities roll out.
What G2 customers like about ThreatDown:
“Help from the seller is never required, however in the event you ever want it, be affected person. First-level help personnel are very pleasant and keen to assist, however they’ve restricted data. Second-level help personnel are nice and able to fixing any issues, however they take a very long time to reply.”
– ThreatDown Evaluation, Yuri Ok.
5. Blackpoint Cyber: Greatest for MSPs and IT-focused groups
Blackpoint Cyber stored arising as a standout, particularly for IT and security-focused corporations that want proactive protection with out a number of further complexity. From all the things I’ve learn, it has constructed a robust popularity not only for managed detection, however for combining that with quick, hands-on risk searching.
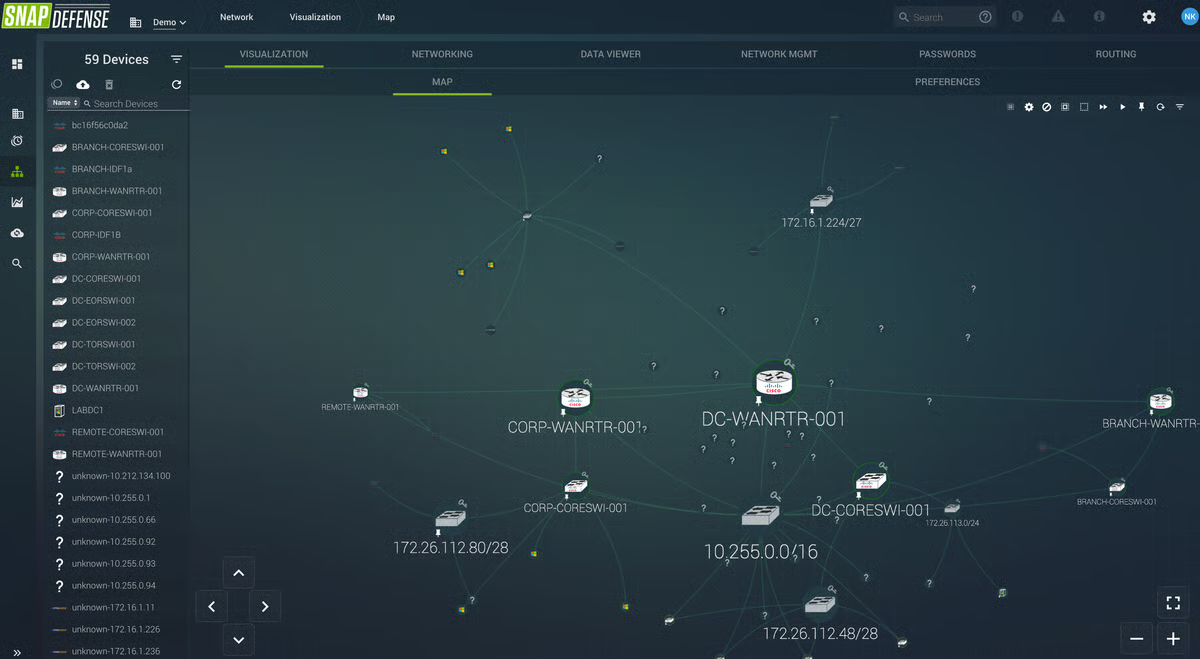
I used to be struck by how unapologetically centered Blackpoint is on stopping threats quick, not simply detecting them. In a number of MDR choices, you see distributors spotlight visibility and alerting as the primary promoting factors. Blackpoint actually does that, however what makes it stand out is how a lot emphasis it places on stay response and containment baked proper into the service.
One factor I discovered particularly notable is that you could name in immediately if one thing pressing occurs, as an alternative of relying solely on tickets or e-mail updates. Whereas loads of different MDR suppliers supply containment and remediation, Blackpoint’s method feels a bit extra private and instant. You may really discuss to somebody in real-time whereas they kill malicious processes or take away persistence, which might make an enormous distinction when each minute counts.
On the core of Blackpoint’s method is its proprietary stay community map — a real-time visualization of all of the hosts and consumer periods in your setting, exhibiting precisely how units and accounts are linked. That stage of visibility pairs nicely with their give attention to hands-on response.
One other robust level is how Blackpoint handles 24/7 monitoring with out burdening clients with extreme configuration. From what I’ve gathered, many of the detection logic and workflows are prebuilt and tuned by their group, so even smaller safety groups can deploy them with out spending weeks organising customized detection guidelines. And the G2 Information backs this up. The satisfaction rankings for ease of use and setup hover round 94–96%.
I additionally observed the platform is very well-liked with corporations in IT companies and community safety, which is smart given how a lot focus Blackpoint places on real-time containment and retaining friction low.
General, most customers appeared genuinely proud of how Blackpoint delivers on pace and proactive safety, and plenty of evaluations praised how hands-off the day-to-day administration feels. That mentioned, there have been a couple of limitations that have been shared by customers on G2.
I got here throughout suggestions about pricing, with some reviewers saying it could really feel costly for smaller companies or budget-conscious organizations. Even so, most individuals agreed that the mix of stay response and powerful help made it well worth the funding, particularly in the event you worth an answer that takes actual motion when one thing goes incorrect.
I additionally got here throughout some suggestions noting that the online portal has room for enchancment, with a couple of customers mentioning that the expertise could possibly be smoother. However these have been far and few in between, and a few additionally famous that current updates have made it higher.
From all the things I’ve seen, Blackpoint Cyber is price severe consideration in the event you worth real-time containment, operational simplicity, and a response-oriented mindset.
Together with Huntress, and Sophos MDR, Blackpoint Cyber has earned a popularity as probably the most dependable MDR software program options for IT corporations. So, I’d positively suggest Blackpoint to IT service suppliers, MSPs, or any mid-sized enterprise.
What I like about Blackpoint Cyber:
- I recognize how hands-on the platform is with containment. You may really name in and discuss to somebody whereas they take motion to kill malicious processes or take away persistence, which feels much more instant than ready on tickets.
- I discover it priceless that many of the detection logic is prebuilt and tuned, so that you don’t must spend weeks customizing guidelines earlier than you’re feeling protected.
What G2 customers like about Blackpoint Cyber:
“Blackpoint is nice with figuring out suspicious exercise and making good selections on locking one thing down to forestall compromises. They’ve been very fast with their detections, and it’s at all times a human who reaches out to verify we acknowledge the difficulty and take over with the subsequent steps.
The incident response stories are nice and similar to those my group makes, which actually cuts down on duplicated efforts. We have been capable of deploy Blackpoint shortly and simply. Blackpoint has an integration with our PSA, permitting us to robotically hold license counts in sync with our agreements. We use Blackpoint now solely as a result of they’ve shortly constructed belief with our group.”
– Blackpoint Cyber Evaluation, Justin H.
What I dislike about Blackpoint Cyber:
- A number of customers talked about that the online portal could possibly be improved to make navigation and general usability smoother, however some additionally famous that current updates have already made it higher.
- I noticed suggestions about pricing feeling excessive for smaller corporations, which could possibly be a hurdle in the event you’re evaluating a number of MDR choices aspect by aspect. However general, most felt the core detection and response capabilities have been robust sufficient that it didn’t maintain them again.
What G2 customers dislike about Blackpoint Cyber:
“BlackPoint Cyber presents robust options, however some could discover the companies pricey, complicated for smaller groups, and infrequently difficult to combine or scale successfully.”
– Blackpoint Cyber Evaluation, Could Anne Y.
6. Purple Canary: Greatest for bigger and extra mature SOCs
I’ll be trustworthy — Purple Canary was a little bit of a brand new discovery for me, and after wanting into it, I’m glad I didn’t overlook it simply because it doesn’t have the largest model footprint.
Beneath the identify (which sounds extra like a code identify than a safety firm) is an MDR platform that persistently will get reward for proactive detection, clear steering, and a genuinely useful help group.
One thing that impressed me is how Purple Canary emphasizes context and readability over quantity, making it simpler to see how every detection impacts your setting. Within the G2 evaluations I learn, customers usually talked about that analysts don’t simply say, “Right here’s a detection”—additionally they clarify why it issues and stroll you thru what to do about it.
That mix of detection, investigation, and training appears like an enormous a part of why groups belief the service, particularly in industries like monetary companies and manufacturing, the place response time and readability are essential.

One other element that makes Purple Canary stand out is the way it manages endpoint telemetry assortment. Fairly than relying solely by itself light-weight agent, Purple Canary can even leverage telemetry from instruments you have already got in place. For instance, integrating with Microsoft Defender or different EDR options.
From all the things I’ve gathered, that flexibility can prevent a number of time in the event you’re not concerned about changing your whole stack simply to get MDR protection.
That being mentioned, I did discover some areas the place customers felt there was room for enchancment. Some groups talked about delays in alerts or getting extra notifications than they anticipated, which may make it tougher to zero in on the highest-priority points.
Others mentioned they’d wish to see extra integrations past what’s presently accessible, particularly to attach Purple Canary extra deeply with their broader safety stack. To be truthful, Purple Canary has shared that increasing integrations is on their roadmap, and most reviewers nonetheless felt the service delivered a number of worth general.
So, from all the things I’ve seen, it’s a strong match for mid-sized corporations and security-focused groups that need enterprise-grade detection with out a number of further baggage.
Please word that Purple Canary was just lately acquired by Zscaler.
What I like about Purple Canary:
- I recognize how thorough and clear the analyst steering is. A number of customers mentioned Purple Canary doesn’t simply ship alerts—it explains precisely why one thing issues and what to do subsequent.
- I discover it priceless that you could leverage telemetry from present instruments like Microsoft Defender and Crowdstrike, so that you don’t have to tear out what you have already got to get full protection.
What G2 customers like about Purple Canary:
“Implementation, ease of use, and buyer help are 3 of the primary issues that Purple Canary goes above and past with. Within the tech trade, we have all skilled very unhelpful help, and in the case of our safety posture, it permits us to “set and neglect” a number of the triggers that we see every day. Their group has been instrumental in steering us in the direction of success, whether or not it is month-to-month conferences, precise malicious triggers, or simply to talk about upcoming safety modifications.”
– Purple Canary Evaluation, Andrew S.
What I dislike about Purple Canary:
- Some reviewers talked about alerts can really feel delayed or too frequent, which typically makes it tougher to give attention to what’s actually pressing.
- I observed suggestions about wanting extra integrations, particularly for groups that depend on a wide range of safety platforms and workflows.
What G2 customers dislike about Purple Canary:
“There’s some lag between the alert in MDE and when RC responds.”
– Purple Canary Evaluation, John C.
Now, there are a couple of extra choices, as talked about beneath, that did not make it to this listing however are nonetheless price contemplating, for my part:
- CrowdStrike Falcon Endpoint Safety Platform: Greatest for corporations that need extremely superior EDR with MDR layered on high. Thought of one of many high managed detection and response companies for tech corporations.
- Secureworks Taegis MDR: Greatest for enterprises that want deep risk intelligence and mature SOC workflows.
- eSentire: Greatest for mid-sized companies that worth a totally managed method and powerful analyst help.
- Expel: Greatest for groups searching for a platform that feels approachable with out sacrificing functionality.
- AlertLogic MDR: Greatest for organizations that need MDR protection throughout hybrid cloud and on-premises environments.
Greatest MDR suppliers software program: Continuously requested questions (FAQs)
Bought extra questions? G2 has the solutions!
Q. Which MDR suppliers are thought of the perfect within the trade?
The perfect-reviewed managed detection and response software program distributors, primarily based on G2 Information, embrace:
- Huntress Managed EDR
- Sophos MDR
- Arctic Wolf
- ThreatDown
- Blackpoint Cyber
- Purple Canary
- CrowdStrike Falcon Full
- Palo Alto Networks (Cortex XDR Managed Menace Looking)
- SentinelOne Vigilance Reply
- Rapid7 Managed Detection and Response
Your best option depends upon your setting, funds, and present instruments.
Q. How do I select the correct MDR service for my enterprise?
When evaluating MDR suppliers, take into account these key standards:
- Protection and scope: Do they defend endpoints, cloud workloads, SaaS apps, and community site visitors?
- Response capabilities: Will they take energetic containment and remediation steps, or simply provide you with a warning?
- Know-how platform: Are they constructed on a proprietary XDR platform or a third-party EDR?
- Integration: Do they combine together with your present SIEM, EDR, and id programs?
- SLAs: What are their ensures for detection, triage, and response occasions?
- Transparency and reporting: How detailed and actionable are their alerts and stories?
- Buyer references: Can they share examples from related organizations or industries?
Q. How shortly can an MDR service be deployed?
Deployment timelines can differ:
- Small or midsize environments: Typically inside 2–4 weeks
- Complicated, hybrid enterprises: Could take 6–12 weeks for full integration and tuning
Most MDR service suppliers supply onboarding help to speed up the method, together with sensor deployment, playbook configuration, and alert tuning.
Q. What’s included in MDR pricing?
MDR pricing usually bundles:
- 24/7 monitoring by safety analysts
- Proactive risk searching
- Incident triage and response actions
- Month-to-month or quarterly reporting
- Menace intelligence feeds
Extra prices can embrace:
- Cloud workload monitoring
- Integration with customized or legacy programs
- Premium response
- SLAs
All the time ask for an in depth proposal to know what’s lined and what’s further.
Q. Can MDR suppliers work with my present EDR or SIEM instruments?
Sure. Many MDR companies are designed to combine with well-liked EDR and SIEM options, corresponding to CrowdStrike, SentinelOne, Microsoft Defender for Endpoint, Splunk, and IBM QRadar.
If you have already got these instruments deployed, MDR suppliers can usually leverage them as an alternative of changing them, lowering prices and deployment time.
Q. What’s the distinction between MDR and XDR? Ought to I take into account each?
MDR is a managed service. Safety specialists monitor, detect, and reply in your behalf. XDR is a know-how platform, a unified toolset aggregating telemetry throughout endpoints, cloud, id, and community to enhance detection.
Some MDR suppliers ship companies on high of their very own XDR platforms, combining automation with human experience. When you lack in-house employees to watch XDR, MDR is commonly the higher match.
Q. Ought to startups get MDR?
Startups ought to strongly take into account MDR in the event that they deal with buyer or monetary information, have compliance necessities, lack in-house safety experience, or are rising past 25–50 workers. MDR gives 24/7 monitoring and knowledgeable response with out the necessity for a full safety group.
When you’re a really small group with no delicate information and powerful safety practices (like MFA and endpoint safety), you could be high-quality delaying MDR till you scale.
Q. Which MDR options are greatest for startups?
A number of the greatest MDR companies for startups are CrowdStrike Falcon Full, SentinelOne Vigilance Reply, Arctic Wolf MDR, Sophos MDR, Purple Canary, and Huntress MDR.
Q. What questions ought to I ask MDR distributors throughout analysis?
Earlier than selecting a supplier, ask:
- What are your detection and response SLAs?
- What platforms and environments do you cowl?
- Do you present containment and remediation, or simply alerting?
- What integrations do you help?
- What does your pricing embrace?
- Do you may have expertise with corporations like mine?
- How do you defend information privateness?
- Are you able to share pattern stories and buyer references?
Handle it proper
After researching dozens of MDR suppliers, learning consumer evaluations, and evaluating capabilities, I’ve come to see that the “greatest” answer isn’t at all times the one with essentially the most subtle instruments. It’s the one which aligns together with your firm’s scale, safety maturity, and sources.
Regardless of your measurement or trade, the choices lined right here replicate expert-recommended MDR software program in your firm, chosen primarily based on real-world suggestions and confirmed efficiency
However finally, MDR isn’t nearly outsourcing safety duties. It’s about constructing a partnership with specialists who may help you shift from a reactive mindset to a extra proactive, resilient method.
Even in the event you’re beginning with restricted sources, the correct supplier can meet you the place you’re and information you ahead step-by-step. Investing time upfront to speak to references, examine real-world experiences, and match every vendor’s strengths to your setting can flip MDR into a real strategic benefit reasonably than simply one other line merchandise in your funds.
Nonetheless on the hunt? Discover our classes of system safety instruments to seek out the perfect match in your safety wants.



