Not too long ago, I underwent a essential buyer escalation. I discussed their product differently that attracted a unfavourable sentiment.
Had I managed and forecasted the chance, it would not have posed questions on my analysis and method.
Simply as in my case, managing, evaluating, and mitigating threat is a urgent concern and an internalized enterprise funding that stops monetary losses or product remembers for companies.
Corporations are continuously scouring the net to research and consider the very best operational threat administration software program to determine contaminated knowledge and craft a threat mitigation technique. Nonetheless, with half-baked knowledge on the web, they find yourself selecting an operational threat administration answer that does not remedy dangers however provides to them.
To grasp how groups mitigate such dangers, I reviewed the 8 finest operational threat administration software program that provide threat mitigation help, appropriate knowledge formatting, and a future-proof option to expose, assess, and eradicate threat in its elementary phases. Let’s get into it!
8 finest operational threat administration software program in 2025: Prime instruments I reviewed
- Pirani: Finest for real-time threat insights and compliance reporting
Delivers stay dashboards and suspicious exercise monitoring ($304/month) - Fusion Framework System: Finest for built-in threat administration
Connects governance, threat, and emergency response processes right into a unified platform (obtainable on request) - IBM OpenPages: Finest for enterprise-scale audit and compliance automation
Gives configurable validation guidelines, audit checklists, and superior reporting ($750/occasion) - Protecht: Finest for structured threat methodology and impression evaluation
Features a strong content material library and frameworks for constant threat analysis (obtainable on request) - Strike Graph: Finest for compliance automation and safety posture administration
Helps hole evaluation, steady monitoring, and anomaly detection within the cloud ($750/month) - Hyperproof: Finest for versatile threat classification and methodology alignment
Simplifies compliance workflows with adaptable frameworks and integrations (obtainable on request) - Ncontracts: Finest for training-driven compliance and threat training
Combines studying modules, safety administration, and content material libraries for governance (obtainable on request) - Oracle Monetary Reporting Compliance Cloud: Finest for enterprise regulatory compliance
Centralizes threat reporting, audit trails, and monetary management monitoring (obtainable on request)
These operational threat administration software program are top-rated of their class, in line with G2’s Spring 2025 Grid Report. I’ve additionally included their month-to-month pricing to facilitate simpler comparisons for you.
Via my analysis, I aimed to curate a personalised listing of appropriate operational threat administration instruments which are straightforward to implement, provide threat compliance and governance, and combine seamlessly with current tech stacks, reminiscent of CRM or ERP.
8 finest operational threat administration instruments that labored
As organizations navigate an more and more advanced regulatory panorama, the demand for operational threat administration software program continues to rise.
Based on latest market research, the worldwide operational risk-management software program market is projected to increase to roughly $11.5 billion by 2033, attaining a CAGR of about 10.6% in the course of the forecast interval. In the meantime, the broader risk-management software program market has projections to achieve $51.97 billion by 2033.
Whether or not you’re struggling to discover a answer that integrates seamlessly along with your API workflows and governance necessities, otherwise you’re in search of a platform with sturdy knowledge integrity that stops corruption in risk-suspected information, the problem stays the identical: balancing functionality with belief.
Past core performance, key concerns reminiscent of implementation prices, worker coaching, documentation high quality, and system scalability persistently emerged in the course of the analysis. For instance, one market report flagged “integration complexities,” “expertise shortages,” and “preliminary funding price pressures” as essential restraints on adoption.
In the end, the purpose isn’t simply to run periodic threat assessments — it’s to construct correct reporting cycles, safe knowledge transfers, and a future-ready infrastructure that anticipates and mitigates evolving dangers.
How did I discover and consider the very best operational threat evaluation software program?
I spent a number of weeks and months analyzing, researching, and evaluating the nitty-gritty of operational threat evaluation software program to study appropriate options that determine, report, and mitigate dangers for organizations.
This evaluation combines my particular person analysis with the feelings of real-time G2 reviewers who possess business expertise. I additionally tried to incorporate key particulars about merchandise, reminiscent of further integrations, hidden prices, software program implementation assets, and so forth, to finish my evaluation.
Moreover, I summarized the highest options, execs, and cons of every product and utilized AI to restructure G2 knowledge right into a digestible format. I additionally used AI to determine frequent sentiments and share them on this article.
In circumstances the place I could not personally check a device as a result of restricted entry, I consulted an expert with hands-on expertise and validated their insights utilizing verified G2 opinions. The screenshots featured on this article could combine these captured utilizing testing and people obtained from the seller’s G2 web page.
What makes an operational threat administration device price it, for my part?
As I’ve emphasised, to stay near precise real-life firm case research and proposals, a super operational threat administration answer must be appropriate with lively community infrastructure, uphold knowledge integrity, and never course of defective threat evaluation reviews, which can lead to important revenue-based chaos.
From stopping knowledge corruption to following authorized and compliance adherence, you must contemplate the following advice earlier than you spend money on operational threat administration software program:
- Plug-and-play frameworks: It’s essential to test whether or not the trendy ORM device provides native integrations, API companies, and connectors for standard enterprise methods, reminiscent of ERP, CRM, GRC, or ITSM instruments. With out this, I consider you threat compatibility points, extended implementation timelines, and extreme reliance on IT. I additionally thought-about their low-code/no-code growth options for speedy deployment.
- Actual-time threat intelligence dashboard: I appeared for real-time monitoring with stay dashboards, threat forecasting, predictive analytics, and dynamic threat scoring. It ought to present a single, unified view of key threat indicators (KRIs), audit trails, and rising threats. This ensures I catch crimson flags earlier than they escalate – relatively than capturing or exploring threat after it has been transformed right into a fatality.
- Granular role-based entry and workflow customization: I additionally evaluated which threat administration software program lets me customise workflows, kinds, alerts, and dashboards for various groups, roles, and areas. That approach, you may drive adoption with out overwhelming customers and enhance device acceptance. I additionally appeared for role-based entry controls (RBAC) to make sure that the best knowledge reaches the best palms with out risking safety or compliance.
- Constructed-in change administration and coaching modules: It’s important to your staff or stakeholders to dedicate time to studying the performance of an operational threat administration device. I looked for related, interactive tutorials, just-in-time coaching prompts, and embedded assist assets to assist customers. Instruments that help self-service onboarding and contextual tooltips will aid you cut back resistance and shorten the training curve, particularly for non-technical employees.
- Regulatory intelligence and compliance automation: It’s essential for the device to offer up-to-date compliance templates, jurisdiction-specific rule engines, and automatic audit trails. I prioritized options like deadline alerts, doc model management, and a centralized coverage library. Having a stringent regulation framework is crucial to shift frameworks with out hiring a military of compliance analysts.
Aside from knowledge compatibility and threat identification, you even have to contemplate whether or not methods can safe and encrypt your dangerous knowledge throughout switch as a result of it’s essential and may be uncovered to knowledge corruption.
Moreover, your focus must be on not solely exposing threat but additionally precisely figuring out the best file, forecasting threat, and crafting a threat mitigation decision. Out of the a number of instruments I shortlisted, the next 8 instruments have been the very best match, for my part.
The listing beneath incorporates real opinions from the Buyer Knowledge Platforms class web page. To be included on this class, software program should,
- Ship numerous methodologies and frameworks for threat administration.
- Embrace customary processes for threat evaluation and mitigation.
- Present workflows to outline and assign duties associated to threat administration.
- Combine and align operational dangers with enterprise processes.
- Adjust to legal guidelines and laws or inner firm insurance policies.
- Monitor the efficiency of operational threat administration actions.
- Analyze operational incidents or losses and their impression on the corporate
*This knowledge was pulled from G2 in 2025. Some opinions could have been edited for readability.
1. Pirani
Pirani is an efficient threat evaluation and administration answer that integrates along with your current CRM or ERP. It identifies and assesses dangers, offering real-time reporting metrics to mitigate and resolve them, thereby safeguarding belongings.
I spent fairly a little bit of time exploring Pirani, and I’ve to say, it has supplied an intuitive expertise for managing operational threat. What impressed me was how user-friendly and approachable the interface is.
I did not want an entire week of onboarding or a robust background in compliance to get began. The platform feels tailor-made to threat professionals who need one thing highly effective but easy. It handles and manages every little thing from registering desks to mapping out controls to categorizing dangers and working audits. Based on G2 Knowledge, 85% of customers worth audit trails and all the knowledge displayed throughout them, together with particulars reminiscent of username, timestamp, or the kind of change required.
One of many standout issues for me is how modular and well-organized the system is. I used to be capable of navigate via threat identification and analysis (each inherent and visible) and even automate components of the management course of.
It is extremely useful that Pirani helps the visible mapping of threat matrices and ties every threat to particular processes and controls. Moreover, I respect how they’ve included dynamic reporting, which is especially helpful.
Once I dug deeper into the subscription tiers, although, that is the place issues acquired a bit extra nuanced. The free plan is restricted. It offers you a style, however you hit the wall fairly quick. You solely acquire entry to fundamental logging options, missing the flexibility to scale and automate reviews.
If you’re critical about integrating Pirani throughout your division, you’ll seemingly outgrow the free tier shortly. The usual plan provides extra threat analysis options, however even then, customers famous that some anticipated functionalities, reminiscent of a customizable dashboard or broader platform integrations, are nonetheless locked behind a premium plan.
What I significantly appreciated within the premium expertise is the automated threat scoring, SARLAFT segmentation, and the flexibility to hyperlink the device with exterior platforms, although some workforce customers did point out a number of ache factors with integrations not being seamless but.
Nonetheless, the platform compensates with stellar help documentation, coaching movies, and a neighborhood that appears genuinely lively and responsive.
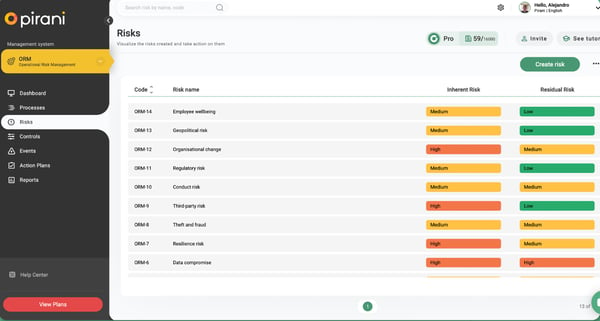
Primarily based on my expertise and the G2 opinions I’ve gathered, Pirani stands out for its sturdy threat administration capabilities and intuitive reporting instruments. Nonetheless, there are a number of challenges price noting.
Efficiency may be inconsistent. At occasions, I’ve skilled sluggish response occasions when switching between modules or producing advanced reviews. Moreover, deleting data nonetheless feels a bit guide, and linking dangers with controls can require extra steps than essential.
Nonetheless, Pirani makes up for these drawbacks with its complete threat analysis options and data-driven forecasting instruments. It offers a safe, structured option to determine, assess, and mitigate dangers successfully, making it a stable alternative for organizations targeted on governance and compliance.
What I like about Pirani:
- I respect how the brand new model of the device offers a number of choices for managing dangers and provides clear knowledge visualization to ship a passable buyer expertise.
- I additionally respect that it’s appropriate with threat methodologies and offers a fantastic diploma of assist in asset administration.
What do G2 Customers like about Pirani:
“I like the standard of the device; I just like the efficiency of the employees who collaborate with us, as they’re all the time prepared to assist and information in every little thing associated to the system or the prevention of cash laundering.”
– Pirani Evaluate, Beylin Patricia R.
What I dislike about Pirani:
- I noticed in G2 opinions mentions of occasional slowdowns when switching modules or producing reviews. Nonetheless, most worth its depth and accuracy for managing advanced dangers.
- I seen structured threat management linking in G2 opinions, though document deletion and affiliation setup can really feel guide. Even so, its safe, data-driven method makes it a dependable alternative for compliance-focused groups.
What do G2 customers dislike about Pirani:
“Provided that it’s a new model of the device, there are nonetheless modules to be developed and a guide facet in numerous parameterization and loading processes that makes the consumer expertise not so good.”
– Pirani Evaluate, Adriana S.
2. Fusion Framework System
Fusion Framework System offers a dependable platform for integrating workflows, processes, and documentation to analyze knowledge, determine essential areas, and make reliable choices.
It additionally automates sure packages to cut back uncertainties and optimizes the chance detection course of to make your workflows extra dependable and safe.
I’ve been utilizing the Fusion Framework System for some time now, and it is develop into a key a part of managing operational threat and enterprise continuity. One of many first issues I seen was the system’s flexibility.
It’s constructed on the Salesforce platform, which suggests you may customise it in nearly any approach you want. Whether or not you’re establishing dashboards, creating workflows, or adjusting knowledge visualization, the system offers you lots of management.
What I’ve discovered essentially the most useful is how completely different components of the platform join with one another. The incident administration options, for instance, are usually not standalone however tie into your total threat and continuity planning.
That has been helpful after we needed to reply shortly to points and monitor how every little thing is being resolved. The reporting instruments additionally work nicely for sharing updates with management.
I’ve pulled collectively clear visuals and summaries with out spending lots of time formatting or explaining the information.
I additionally cherished the robustness of integration capabilities. With the ability to herald transformation from different methods has made it simpler to see the total image whereas assessing dangers. It has additionally helped with planning as a result of we’re not working in silos. We’ve got knowledge flowing in between platforms, which makes every little thing extra correct and well timed.
The automation options additionally saved us time, particularly when establishing recurring duties and reminders associated to threat assessments or compliance checks.
However Fusion is not one thing you may simply log into and begin utilizing immediately. As a result of it’s so customizable, setting it requires a little bit of effort. We had to spend so much of time with product help to configure the system to suit our wants.
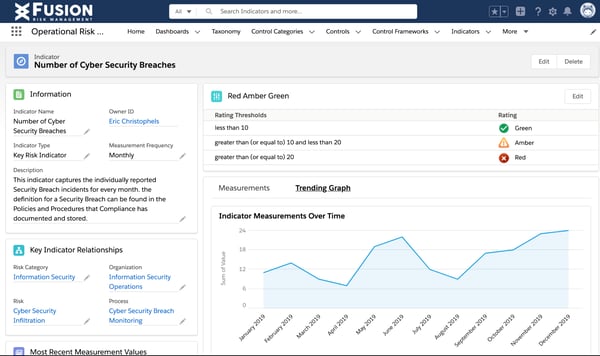
Primarily based on my evaluate of G2 opinions and private expertise, the Fusion Framework System offers highly effective instruments for managing threat, enhancing safety, and streamlining processes throughout groups. That stated, the expertise isn’t with out challenges. Whereas help was usually useful, it may typically be difficult to seek out somebody aware of particular use circumstances, seemingly as a result of workforce turnover, which often resulted in slower response occasions.
I additionally discovered the interface to be overwhelming at first. With so many menus and settings, new customers might have further coaching to get comfy. And since some superior options, reminiscent of real-time dashboards and higher-tier help, are locked behind premium plans, it’s price contemplating your price range earlier than investing.
Nonetheless, as soon as carried out, the Fusion Framework System excels at what it’s constructed for: monitoring assets, refining workflows, and mitigating threat. For organizations targeted on operational resilience and compliance, it’s a complete and efficient answer.
What I like about Fusion Framework System:
- I cherished that the Fusion Framework System permits corporations to have a single place to be taught, put together, and reply to any enterprise threat they could face.
- One other facet I cherished is the integrations, as they allowed me to include knowledge from any context or information base.
What do G2 Customers like about Fusion Framework System:
“I just like the simplified method and the automation of processes. It has additionally been useful that it’s customizable and versatile, permitting us to have a superb overview and be feature-rich. Furthermore, the benefit of use of role-based entry management is great as a result of it permits us to assign companies and elements, and it exceeded my expectations.”
–Fusion Framework System Evaluate, Agung S.
What I dislike about Fusion Framework System:
- I seen that help is mostly useful, although discovering somebody aware of particular use circumstances can take time as a result of workforce turnover. Nonetheless, G2 customers say points are resolved completely as soon as related.
- I noticed that G2 customers talked about the platform is highly effective however can really feel overwhelming at first. Nonetheless, most agree that it delivers sturdy worth in bettering workflows and threat administration.
What do G2 customers dislike about Fusion Framework System:
“One main weak spot of the Fusion Framework System is the flexibleness by which the system may be modified to suit a particular want. Nonetheless, this goes a great distance in creating constraints concerning particular software program customization, therefore some inefficiencies. Furthermore, there could also be minor points, reminiscent of bugs and glitches, which may be irritating and trigger sure inconveniences. These weaknesses have induced, to some extent, a decline in our output price and the location’s usability.”
– Fusion Framework System Evaluate, Sullivan C.
3. IBM OpenPages
IBM OpenPages is a extremely agile and AI-powered governance, threat, and compliance (GRC) administration answer that gives cloud-based companies to handle and analyze risk-based knowledge, enabling the creation of actionable threat administration methods.
In the event you work in GRC, you have in all probability heard of this device. It is undoubtedly not your common device; it is an enterprise-grade platform that integrates a number of shifting components right into a single, cohesive ecosystem.
The most effective factor about the platform is its customizability and responsiveness. It provides complete workflow administration tailor-made exactly to our operational threat administration processes.
The truth that I can configure it to align with our inner audit processes, management frameworks, and compliance checks has made my life really easy. We additionally use IBM’s Watson AI capabilities constructed into OpenPages, particularly the Watson Pure Language Processing integration for threat categorization and root trigger evaluation.
AI helps extract insights from unstructured knowledge, reminiscent of incident reviews and emails, which saves lots of guide work.
I additionally love how scalable the platform is. Whether or not managing operational threat, integrating regulatory compliance, conducting inner audits, managing coverage, or addressing third-party threat, you must entry a unified platform. The truth is, in line with G2 Knowledge, 91% of customers worth the procedures to implementing disaster administration plans and actions.
I began with the core operational threat module, however we expanded into compliance and coverage administration as our wants grew. Every module is actually its personal mini ecosystem, however all of them discuss to one another, which is superb when you get the dangle of it.
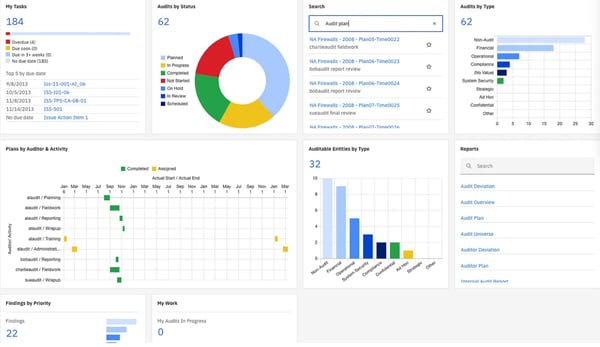
Primarily based on my expertise and the G2 opinions, IBM OpenPages is a strong, enterprise-grade platform for managing threat and compliance. That stated, setup isn’t easy, the implementation course of may be prolonged, and also you’ll seemingly need assistance from IBM consultants until your inner workforce could be very tech-savvy. Nonetheless, as soon as configured, it delivers spectacular automation and management throughout advanced governance workflows.
The interface provides deep performance and professional-grade instruments, however I discovered it much less intuitive than anticipated. The design feels a bit dated, and the training curve is steep, even for skilled customers. Nonetheless, when you get used to it, the vary of capabilities makes it a sturdy device for managing enterprise-level compliance.
Language help is one other combined space. Whereas the platform handles world operations nicely, a few of my non-native English-speaking teammates discovered the translations inconsistent. Even so, its potential to centralize threat knowledge throughout areas is a serious benefit for worldwide groups.
Pricing is the place issues get tough. OpenPages provides highly effective audit, compliance, and Watson AI integrations; nonetheless, most of those options are solely obtainable with higher-tier plans. For us, the funding made sense given the size and safety wants of our group. Nonetheless, smaller groups may discover it arduous to justify the associated fee.
Lastly, the reporting capabilities are extremely detailed and customizable. Nonetheless, they’re not essentially the most intuitive to make use of, and I needed to create templates to simplify the method of producing recurring reviews. As soon as arrange, although, they supply clear, data-rich insights that make governance monitoring far simpler.
General, IBM OpenPages stands out for its depth of compliance and automation, making it a superb alternative for giant organizations managing advanced world threat buildings.
What I like about IBM OpenPages:
- I really like how I can customise the dashboards, views, objects, and reviews to adapt them to the workforce’s particular wants. This helps us make extra knowledgeable choices.
- I additionally respect the way it permits us to take care of all data of inner incidents throughout the group and monitor key threat indicators.
What do G2 Customers like about IBM OpenPages:
“This platform is scalable; it suits our firm measurement nicely. I really like this platform as a result of it permits customization. It is extremely good for managing dangers via its GRC software program. It has additionally streamlined compliance with evolving laws.”
–IBM OpenPages Evaluate, Edz R.
What I dislike about IBM OpenPages:
- I noticed that G2 customers talked about the setup may be prolonged and sometimes requires the help of IBM consultants to make sure every little thing runs easily. Nonetheless, as soon as carried out, it delivers sturdy, scalable compliance capabilities for giant organizations.
- I noticed that the platform’s options are strong and data-driven, however many superior instruments are solely accessible behind premium tiers, making it costly for smaller groups. Even so, those that spend money on greater plans profit from distinctive reporting,
What do G2 customers dislike about IBM OpenPages:
“Though IBM Watson NLC helps a number of main languages, there could also be limitations when working with much less generally used languages or dialects. Customers working with non-mainstream languages may face challenges in attaining the identical accuracy and precision as they’d with extra broadly supported languages. Nonetheless, IBM regularly expands its language protection, so this limitation could enhance over time.”
– IBM OpenPages Evaluate, Tiago O.
Take a look at my peer’s evaluation of the finest GRC software program in 2025 and dive into her particular person takeaways for each platform to strategize your threat administration points properly.
4. Protecht
Protecht is an enterprise threat administration platform that displays all incidents, investigates dangers, and units periodic threat assessments to dynamically consider and mitigate any threat prevalence.
Once I first began evaluating Protecht, I wasn’t fairly certain what to anticipate. However over time, I’ve come to understand how a lot it may well assist arrange and handle dangers throughout completely different components of a enterprise.
It is particularly helpful should you deal with duties reminiscent of compliance, audits, incident reporting, or enterprise threat administration.
What stood out to me early on was how a lot I may regulate the platform to swimsuit the way in which our workforce works. I did not really feel like I needed to pressure my course of into the system as a result of there was flexibility to make it work for us.
Establishing threat registers and reporting instruments was easy as soon as I turned aware of them. I loved having the ability to create detailed reviews and dashboards that drew knowledge from a number of sources. Moreover, the real-time insights enabled me to remain up to the mark with out continuously chasing updates.
The system additionally made it simpler to handle various kinds of registers, reminiscent of dangers, incidents, and audits, multi functional place. Not having to leap between instruments saved lots of time.
The customization choices have been useful, particularly for automated workflows and notification settings. I did not know the right way to code to make adjustments, which was a aid. If I ever acquired caught, their help workforce all the time responded promptly and supplied useful help, which made a major distinction throughout setup and configuration.
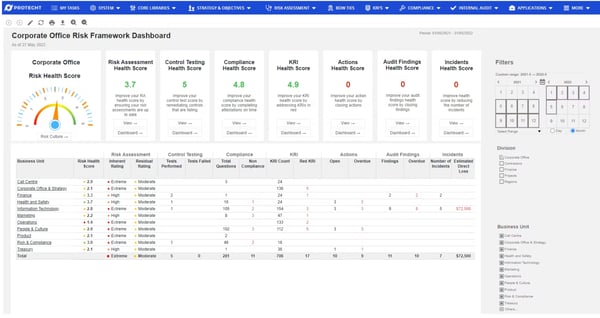
Primarily based on my expertise and what I’ve seen mirrored in G2 opinions, Protecht offers a sturdy, safe platform for managing threat and making certain compliance. That stated, I did face a number of challenges alongside the way in which. The educational curve may be considerably steep, and a few areas of the platform could really feel extra advanced than essential. Nonetheless, when you get aware of it, the depth of performance turns into certainly one of its greatest strengths.
The interface itself is stable, however not essentially the most trendy or intuitive. Navigating via settings can take some getting used to, and I seen that superior options, reminiscent of detailed dashboards and analytics, are solely obtainable in higher-tier plans. Whereas that felt limiting at first, these upgraded instruments ship spectacular insights as soon as unlocked.
Integration was one other space that required some further effort. Connecting Protecht with BI instruments or inner methods wasn’t precisely plug-and-play, and I discovered myself reaching out to help a number of occasions for steerage. Even so, the help workforce was responsive, and as soon as every little thing was arrange, the integrations labored easily.
General, regardless of a number of hurdles, Protecht stands out as a safe and complete threat administration platform. It offers dependable audit trails, sturdy GRC compliance instruments, and correct threat evaluation, making it a trusted alternative for organizations that take threat governance critically.
What I like about Protecht:
- I respect the customizability and suppleness that Protecht provides, which permits to tailor our workflows and necessities.
- I used to be additionally impressed by how Protecht automates every little thing in a threat administration system, from starters to leavers, from audits to assessments, and from insurance policies to procedures.
What do G2 Customers like about Protecht:
“Protecht provides a seamless expertise for customers in search of strong and customizable options tailor-made to the enterprise’s particular necessities. One of many standout options is the system’s flexibility, which permits customers to simply replace the system to fulfill their distinctive wants. Whether or not configuring threat registers, designing workflows, or producing customized reviews, the platform empowers the consumer to adapt it to match their particular wants. This helps improve consumer satisfaction and permits the enterprise to align the system with its current processes.”
– Protecht Evaluate, Que N.
What I dislike about Protecht:
- I noticed G2 customers point out that the interface feels a bit dated, though its depth and reliability make up for it when you develop into aware of the platform.
- I noticed G2 customers point out that the integrations and superior analytics aren’t plug-and-play and sometimes require higher-tier plans. Nonetheless, with stable help and setup, they provide wonderful insights and efficiency.
What do G2 customers dislike about Protecht:
“As with every vendor-sourced merchandise, there are pure limitations to growth and performance. So one of many constraints is the necessity to have interaction with Protecht to make the extra important adjustments to options and performance distinctive to our wants.”
– Protecht Evaluate, Raj H.
5. Strike Graph
Strike Graph is a compliance administration device that ensures adherence to GDPR, HIPAA, CMMC, NIST, ISO 27001, SOC 2, and PCI DSS protocols, in addition to different safety certifications, to monitor, mitigate, and eliminate unidentified threats inside the system.
I’ve been utilizing Strike Graph for some time now to handle our compliance journey, with a main deal with SOC 2, in addition to ISO 27001 and HIPAA frameworks. Based on G2 Knowledge, 89% customers worth its compliance monitoring performance.
When you have ever tried navigating the tangled internet of GRC with out correct tooling, Strike Graph feels as when you have been given all of the assets to handle your processes.
What initially caught my consideration was the dashboard. It is not simply clear however alive and intuitive. It offers a dynamic overview of your present standing throughout numerous controls, audits, and proof submissions.
Even workforce members who weren’t seasoned compliance specialists may navigate it with no need a ten-part tutorial. The proof add stream was extraordinarily clean. You’ll be able to drag and drop or hyperlink gadgets, and the system really remembers the context, like expiry timelines or reuse choices throughout frameworks. That is big.
I additionally love the predefined template gallery. Strike Graph features a complete useful resource library with pre-built templates for insurance policies and controls that saved us numerous hours. It is particularly useful in case you are beginning recent with compliance or making an attempt to standardize your inner documentation.
The templates comply with finest practices and align tightly with audit requirements, which gave me extra confidence throughout our prep work.
One other standout for me is the workforce help. I’ve had well timed responses from their specialists at any time when I wanted steerage. I did not should chase anybody down, take care of ticketing methods, or endure lengthy wait occasions to get solutions to my queries.
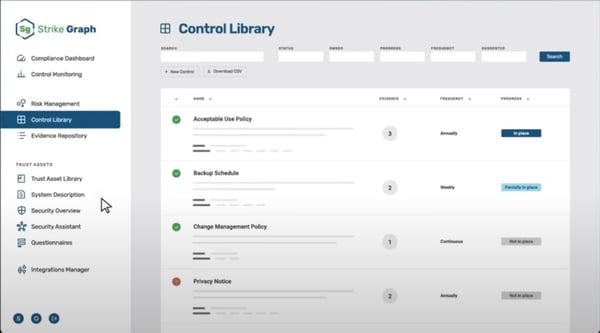
What I’ve seen in G2 opinions, Strike Graph is a robust platform for managing compliance and audit readiness, however there are a number of areas that could possibly be improved.
The reminders and admin alerts could possibly be extra detailed, particularly round certification timelines and guideline updates. I additionally would’ve appreciated extra private touchpoints, like common check-ins or a devoted account supervisor, because the expertise can really feel a bit hands-off as soon as onboarding is full.
From what I can inform, the essential plan contains a lot of the necessities, proof uploads, templates, and a easy compliance tracker. Nonetheless, the upper tiers unlock much more worth, providing automated framework mapping, AWS integrations, threat scoring, and enhanced audit reporting. These superior instruments save groups appreciable time when managing a number of frameworks or making ready for exterior audits.
That stated, Strike Graph stays a dependable answer for staying aligned with safety and compliance requirements. It helps preserve inner audit trails, centralize proof, and guarantee ongoing readiness throughout advanced compliance packages.
What I like about Strike Graph:
- I cherished the Strike Graph dashboard, because it made it straightforward to see progress and present essential duties with out trying on the full listing of controls and proof.
- I additionally discover periodic reminders about expiring proof very useful for maintaining monitor of what must be refreshed.
What do G2 Customers like about Strike Graph:
“Strike Graph makes the SOC 2 compliance course of simpler to grasp by automating a big portion of our workforce’s effort— their workforce’s sensible help throughout audits is essential and lowers nervousness and confusion.”
– Strike Graph Evaluate, Christian D.
What I dislike about Strike Graph:
- I seen G2 customers point out that they wished reminders and admin alerts to be extra detailed. Nonetheless, its automation instruments make ongoing compliance straightforward to handle.
- I noticed G2 customers point out that the upper tiers add important worth with framework mapping, AWS integrations, and audit reporting. Even so, most G2 customers discover the upgrades worthwhile for his or her advanced compliance wants.
What do G2 customers dislike about Strike Graph:
“For customers new to compliance administration software program, some issues is probably not apparent, so it takes time to adapt. Additionally, there could possibly be extra examples of the items of proof which are required for sure controls.”
– Strike Graph Evaluate, Dimitri Okay.
6. Hyperproof
Hyperproof is a safety and compliance administration device that automates essential processes, displays incidents, and helps corporations keep compliant with laws and mitigate dangers.
Truthfully, Hyperproof has been a game-changer for the way I handle compliance and operational threat throughout the group. From the very first interplay, what stood out to me was how intuitive and user-friendly the platform is. I did not have to sit down via hours of coaching or dig via an awesome consumer guide.
It contains a light-weight, responsive UI that makes duties simpler to assign and proof linking smoother throughout a number of frameworks.
What I genuinely love about Hyperproof is its centralization. Managing paperwork, mapping controls, and monitoring proof are multi functional place. I’ve used different GRC instruments, which are likely to scatter the functionalities or add new options that do not fairly match.
However with Hyperproof, every little thing feels prefer it belongs right here. Their management mapping function, particularly, is implausible. I can hyperlink controls to a number of requirements, reminiscent of SOC 2, ISO 27001, and HIPAA, which saves a major quantity of redundant work.
There may be additionally a Hypersync integration that automates proof assortment from exterior methods, reminiscent of Jira, Slack, Google Workspace, and AWS. This alone cuts our audit time and saves effort.
This device additionally excels to making ready for assessments or opinions. It guides you step-by-step, from documentation to activity monitoring to proof validation. Throughout our final SOC 2 audit, I utilized Hyperproof’s audit workspace, which routinely compiled all management proof and audit trails right into a single location. I did not even should e mail our auditor individually.
Hyperproof additionally lets me handle a number of compliance frameworks in parallel, due to its multi-program construction. I can assign controls that apply throughout requirements and construct a single supply of reality. Their labeling system and permissions mannequin give me granular controls over who sees what. This makes collaboration with completely different departments (IT, authorized, and HR) clean and environment friendly.
I additionally need to spotlight Hyperproof’s customization talents. Whether or not I’m constructing dashboards, configuring workflows, or establishing notifications, I can simply accomplish all of those duties.
It adapts to your current processes, not the opposite approach round. And for enterprise clients, it solely will get higher. Premium options in high-tier plans, like customized proof retention insurance policies, superior role-based entry management, and managed service help, make it seamless to scale compliance.
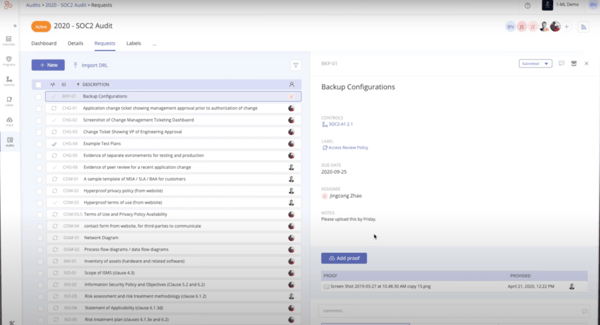
From my expertise and what I’ve seen echoed in G2 opinions, Hyperproof is a strong, all-in-one compliance platform that makes it straightforward to streamline workflows, combine with ERP and CRM methods, and monitor audit controls to remain aligned with laws.
That stated, some areas could possibly be smoother, sure components of the dashboard really feel a bit inflexible, and reporting customization isn’t as versatile as I’d like. Nonetheless, the platform’s total construction and automation instruments make compliance administration much more environment friendly and clear.
I additionally seen that establishing advanced compliance packages can take time. Even workforce members with prior expertise discovered the training curve steeper than anticipated. That stated, when you get previous onboarding, the platform’s flexibility and depth actually begin to shine. I’d like to see Hyperproof add extra guided setup wizards or in-app tutorials to make the preliminary setup simpler.
The product workforce is nice about rolling out new options often, although documentation updates can often lag behind these adjustments. Nonetheless, Hyperproof stays a dependable, compliance-first answer that gives the construction, visibility, and integrations companies want to remain audit-ready and confidently mitigate threat.
What I like about Hyperproof:
- I really like how Hyperproof has a modern interface, is simple to implement, and requires no further coaching.
- I additionally respect the way it makes automating a GRC program really easy and attainable. It provides API connections to frequent infosec instruments and is extraordinarily straightforward to arrange.
What do G2 Customers like about Hyperproof:
“One of many elements I respect most about Hyperproof is its potential to centralize and streamline compliance administration. It is spectacular the way it consolidates insurance policies, procedures, controls, proof, and threat monitoring right into a single platform. This eliminates the chaos of spreadsheets and guide monitoring, which may be extremely time-consuming and error-prone.”
–Hyperproof Evaluate, Venkata R.
What I dislike about Hyperproof:
- I noticed in G2 consumer opinions that Hyperproof streamlines compliance processes and integrates nicely with ERP and CRM instruments. That stated, components of the dashboard really feel inflexible, and the reporting could possibly be extra versatile; nonetheless, its automation and visibility options make up for it.
- I seen G2 customers point out that the platform can initially really feel advanced, particularly when constructing compliance packages from scratch. Nonetheless, as soon as arrange, it’s highly effective and dependable, splendid for sustaining audit readiness and mitigating threat.
What do G2 customers dislike about Hyperproof:
“The dashboards in Hyperproof could possibly be upgraded to show extra significant knowledge. For instance, present trending charts of points open and closed over time.”
– Hyperproof Evaluate, Jay L.
7. NContracts
NContracts provides threat mitigation, threat evaluation, threat evaluation dashboards, and compliance help to fintech corporations, credit score unions, mortgage corporations, and banks.
As somebody who expresses a fantastic curiosity in compliance and threat administration, I’ve come to depend on NContracts, because it balances each and helps monitor potential errors.
What I actually like is how the platform brings collectively numerous elements of threat oversight. It isn’t only a dashboard with scattered charts. NContracts pulls in insights from throughout departments, giving me a cohesive view of our organizational threat.
Whether or not I’m reviewing third-party threat or inner coverage gaps, the device offers the knowledge that issues most. The interface is clear and fairly intuitive, so I don’t waste hours making an attempt to determine the place to seek out issues.
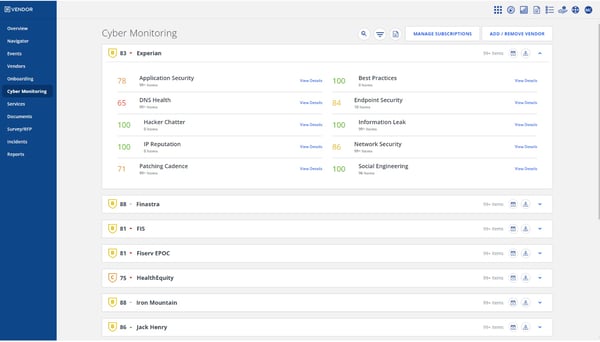
Primarily based on my expertise and what I’ve seen in G2 opinions, Ncontracts excels at offering complete threat evaluation and compliance alignment throughout essential data-driven workflows. It’s a sturdy platform that helps groups consider threat, guarantee correct governance, and keep compliant with authorized insurance policies.
That stated, it’s not with out its flaws. I’ve seen that some methods don’t combine as seamlessly as they need to, which often forces me to change between modules that ought to really feel extra related, particularly when assessing dangers throughout a number of departments. Nonetheless, as soon as every little thing is configured, the depth of perception and reporting it delivers is spectacular.
I’ve additionally seen a slight lag in rolling out new options. The instruments I used to be anticipating took longer to launch than anticipated. Even so, the platform stays a stable, end-to-end answer for compliance and threat administration, particularly for groups that want a unified view of their governance framework.
What I like about NContracts:
- What I like finest about NContracts is that now we have one system to trace all our findings, retailer enterprise threat assessments, and handle distributors.
- I additionally cherished how the platform was straightforward to configure whereas offering some flexibility to permit us to customise our report fields and make adjustments.
What do G2 Customers like about NContracts:
“I’ve solely been utilizing the software program for a 12 months and discover it very user-friendly. We’ve got invested in a number of of the packages provided and discover them very helpful, particularly Nvendor. I benefit from the colourful personalization and dashboard, as I exploit it typically. It makes it seamless to take care of our distributors. If I ever have any questions or want help, the help workforce is all the time prepared to assist and could be very educated. I’d advocate this product.”
–NContracts Evaluate, Leeann P.
What I dislike about NContracts:
- I seen that some modules don’t combine as easily as they need to, which might sluggish cross-department assessments. Nonetheless, as soon as arrange, G2 customers point out that it provides clear, data-driven insights that make compliance administration simpler.
- I noticed that function rollouts can take longer than anticipated. Even so, I seen that G2 customers discuss its reliability and depth, making it a robust alternative for organizations prioritizing governance and threat management.
What do G2 customers dislike about NContracts:
“Though there may be good info concerning step-by-step processes to make the most of the system, I wish to acquire further steerage when setting the potential publicity of “Monetary Publicity” dangers.”
– NContracts Evaluate, Stacia H.
8. Oracle Monetary Reporting Compliance Cloud
Oracle Monetary Reporting Compliance Cloud is a monetary reporting and threat management device that helps you categorize, forecast, and management threat related to consumer workflows, cost particulars, and different monetary service procedures.
It additionally optimizes processes for inner and exterior controls through the use of the Oracle ERP cloud deployment function, so your group adheres to compliance laws.
Oracle Monetary Reporting Cloud centralized all threat and compliance operations right into a single cloud-based platform for me and my groups. That alone saved my workforce a ton of time that may’ve in any other case been spent switching between completely different instruments.
As a result of it is a cloud answer, I may assess every little thing, reminiscent of threat assessments, monetary reporting workflows, and inner audit checklists, from actually wherever.
For a distant or hybrid setup, you’ve the flexibleness of logging in from wherever at any time, with out the necessity for a VPN or server limitations, which makes the device extremely trendy and scalable.
Nonetheless, the preliminary scaling up was a bit of labor. For groups new to Oracle’s cloud ecosystem, the preliminary configuration course of may be time-consuming. In case your workforce does not have Oracle Cloud expertise, you must consult with documentation and help throughout implementation.
As soon as we have been up and working, nonetheless, the interface proved to be a nice shock. It isn’t overly flashy, however it’s intuitive. I cherished how every little thing was laid out clearly. Visible dashboards and knowledge visualization instruments can help you outline enterprise processes, assess potential dangers, and monitor compliance.
The reporting capabilities are particularly stable. With only a few clicks, you get a full snapshot of what is going on on throughout processes. I typically use the built-in templates to run real-time threat assessments and generate audit trails. These templates are strong, though some area of interest companies could must customise them to fulfill their particular wants.
Integration is one other main plus. Oracle FRC integrates properly with different Oracle instruments, particularly ERP or GRC methods, which made our finance workforce’s life rather a lot simpler.
Moreover, it displays compliance and regulatory processes utilizing automated frameworks and pre-configured templates that cowl most business requirements. I’ve even seen it spotlight what we did not initially suppose could be a compliance threat as a result of its automated steady monitoring options.
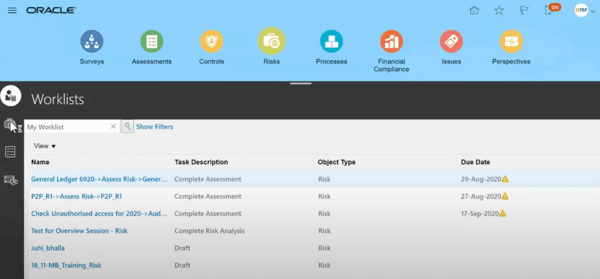
Nonetheless, there are a number of areas the place Oracle FRC can enhance. Whereas the platform retains bettering, there may be all the time room for extra dynamic options. For instance, it would be extraordinarily useful to have instantaneous guided demos seem when new updates are launched. It might clean the training course of, relatively than forcing us to learn manuals or look ahead to IT walkthroughs.
The product workforce appears responsive, and there are common product updates that maintain the platform updated.
By way of pricing tiers or plan ranges, a lot of the premium worth seems to be packed into the usual enterprise cloud package deal. There isn’t any clear freemium or light-weight model; it is vitally a lot an enterprise-first product. Nonetheless, this additionally comes with highly effective instruments for compliance monitoring, audit administration, threat mapping, and management testing.
General, Oracle FRC is an enterprise-first threat administration answer that may authenticate your each day workflows, run compliance audits, monitor incidents, and forecast threat technique for you and your groups.
What I like about Oracle Monetary Reporting Compliance Cloud:
- I really like how Oracle Reporting Compliance Cloud provides reporting and analytical instruments that may generate compliance reviews, saving a major period of time.
- I additionally discovered that the intuitive dashboard makes it very simple to outline enterprise processes, determine dangers, and forestall dangers.
What do G2 Customers like about Oracle Monetary Reporting Compliance Cloud:
“A cloud answer for threat info reporting and documentation for regulatory compliance. The product is intuitive to grasp.”
–Oracle Monetary Reporting Compliance Cloud Evaluate, Verified Consumer in Accounting
What I dislike about Oracle Monetary Reporting Compliance Cloud:
- I seen that whereas Oracle provides a complete threat administration suite, the preliminary setup and configuration may be very advanced for organizations with no prior expertise with Oracle merchandise. G2 opinions discuss this, too.
- I noticed that G2 customers had entry to many built-in templates and options, which required companies to customise their workflows, thereby including to the implementation price and time.
What do G2 customers dislike about Oracle Monetary Reporting Compliance Cloud:
“I have not confronted any massive points whereas utilizing the cloud. Nonetheless, there are some efficiency points, significantly with massive knowledge throughout peak utilization, which may be negligible as it isn’t a serious challenge.”
– Oracle Monetary Reporting Compliance Cloud Evaluate, Sai D.
Finest operational threat administration software program: Continuously requested questions (FAQs)
1. What’s the finest operational threat administration software program for startups?
For startups that want scalable but easy-to-use instruments, Pirani and Strike Graph are splendid. Pirani provides intuitive dashboards and fast onboarding with real-time threat insights, whereas Strike Graph automates compliance processes, reminiscent of SOC 2 and ISO 27001, saving time for lean groups.
2. What are the main operational threat administration options for medium-sized companies?
Protecht and Hyperproof stand out for medium-sized companies. Protecht provides versatile threat workflows and automation with out requiring heavy coding, whereas Hyperproof integrates with Jira, Slack, and Google Workspace — making it splendid for mid-tier groups managing a number of compliance frameworks.
3. What are the top-rated operational threat software program for company use?
Enterprises belief IBM OpenPages and Oracle Monetary Reporting Compliance Cloud. Each present enterprise-grade compliance automation, AI-assisted threat categorization, and world scalability — splendid for companies dealing with cross-border laws and audit-heavy environments.
4. Which operational threat app is finest for small enterprise use?
Pirani is the very best match for small companies. It’s inexpensive, user-friendly, and offers sturdy threat visualization and audit trails even at decrease pricing tiers, serving to small groups strengthen governance with out deep technical experience.
5. What are the simplest threat administration instruments for service corporations?
Service-focused organizations profit from Fusion Framework System and NContracts. Fusion unifies governance, threat, and response workflows, whereas NContracts helps handle vendor relationships, inner audits, and regulatory compliance — essential for service-driven industries.
6. What are the favored operational threat platforms for expertise corporations?
Hyperproof and Strike Graph are the go-to platforms for tech corporations. Each provide seamless integrations with cloud ecosystems, automate proof assortment, and preserve ongoing audit readiness — key for SaaS and IT corporations needing fixed compliance visibility.
7. What’s the very best operational threat software program utilized by business leaders?
Trade leaders persistently depend on IBM OpenPages and Oracle FRC Cloud. These platforms ship AI-powered governance, predictive analytics, and unified audit management, supporting advanced, multinational operations throughout regulated industries like finance and manufacturing.
8. What are the very best ORM methods for lowering software program venture dangers?
Hyperproof and Fusion Framework System excel right here. They centralize documentation, assign threat possession, and automate compliance monitoring — making certain software program groups catch course of and safety gaps early within the growth lifecycle.
9. Which operational threat software program provides the very best buyer help?
Pirani and Strike Graph lead in consumer satisfaction. G2 reviewers spotlight their proactive groups, responsive coaching assets, and lively neighborhood help — serving to customers resolve points quicker and maximize ROI.
10. What are the very best operational threat instruments for app builders?
App builders favor Hyperproof for its developer-friendly integrations (e.g., API-based workflows, ERP, and CRM sync) and Strike Graph for automated safety compliance mapping. Each instruments simplify threat assessments inside agile environments.
Nip the chance within the bud
Selecting an operational threat administration software program will depend on a number of components, together with the severity of your threat, the dimensions and composition of your workforce, the necessity for added employees coaching, compliance measures, software program compatibility, and scalability.
Whereas all of the software program in my evaluation checked out these necessities, as a enterprise, you must issue in additional revenue-based parameters and implementation timelines to make a agency determination. When you’re at it, be happy to return to this listing for a fast look.
Monitoring your cloud knowledge in silos? Test my peer’s evaluation of 30+ finest cloud monitoring instruments in 2025 to retailer and defend your knowledge on the cloud.



